Cyber-security is something that everybody should pay a lot of attention to, especially in 2024. With every new year, experts say that the number of breaches, identity stealing, and other sorts of cyber-criminal is only getting more frequent. They believe that in the future, people won’t be physically stealing anything, and everything will be done through a computer.
Although it takes a skilled person, someone with a lot of computer knowledge, training and experience to do some of the cyber-crimes we mentioned above, it’s still not as rare to become the victim of someone like that, so “It won’t happen to me out of all the people” is not a valid argument when somebody asks why you aren’t investing in security tools.
In this article, we are going to help you learn some more about cyber-criminal in general, how and why it happens, and what some of the best ways to protect yourself are. If you are interested in learning some more, feel free to read until the end.
Protecting yourself online

When it comes to staying safe while browsing the internet, you are the only person who can increase your chances if you are being careful enough. This means that if you are paying enough attention to which websites you are visiting and what kind of content you are viewing, you can greatly reduce the chances of something bad happening to your PC or the valuable information you have stored in it.
One of the best ways to do this is by double-checking if the websites that you are visiting are the official ones, and there aren’t any hidden things in the URL which point out that it’s a fake website. Also, when you are required to make an account or write your username and password, always make sure that the website is secure and it has the small little lock symbol right on the left of the URL bar.
This ensures that your information is not being sent anywhere upon logging in. However, sometimes no matter how careful we are, someone with bad intentions can still target us, and this is when we need some real help from sophisticated cyber-security software.
1. SolarWinds Manager
Very sophisticated software that helps people stay completely safe while browsing the internet. The dashboard is very detailed and it is meant for advanced users, although beginners can use it as well. The computer program uses real-time monitoring and it will report anything suspicious that’s coming your way on the network.
What’s good is the fact that in every new update, the so-called “threat intelligence system” gets better and improved, meaning that the developers care about the software and they don’t stop working on it ever.
The log, or library, gets constantly updated and new types of threads are being indexed, helping future users remain safe even from something that’s considered to be a new type of security threat. We recommend it and we think that you should give it a try.
2. A VPN

Not many people use a VPN, but it’s the staple of internet security and it should be used even by not-so-advanced computer users. VPN stands for a Virtual Private Network (find out more visit this website), and it VPN stands for a Virtual Private Network, and it helps you browse the internet completely anonymously by hiding your IP address through a “tunnel”, masking it with a different one. By doing this, you will appear as a user from a completely different country when someone tries to find your location.
There are truly numerous choices on the market when it comes to choosing a virtual private network software, but our recommendation is to check vpnside.com and find all of the best ones there.
The difference in quality and functionality between VPN’s is sometimes huge, so take your time and don’t rush when you’re choosing one that will be your main go-to VPN for daily browsing.
3. Intruder
If you are the owner of a business, and you are looking to find the best monitoring tool that will prevent possible breaches and invasions that can cause a lot of damage, you might want to take a better look at Intruder, the world’s most popular cloud-based scanner that you can have nowadays.
This software provides a very detailed report about anything that even slightly appears as a possible weakness in your network, so you can use it to create an impenetrable “wall” that protects your valuable data and confidential business information.
The log of Intruder is constantly being updated, so you will never be caught off-guard by some new type of a breaching method that you haven’t heard of yet. You can have as many user accounts as you want to be connected to Intruder, and you can do as many scans as you want on your network. A truly amazing software.
4. Wireshark
Let’s take a look at a free yet very useful software called Wireshark, something that can help you trade all of the IP-addresses of people who want to do anything fishy on your network. We all know how important finding evidence is when you are trying to prove that someone is trying to virtually harm you, so without getting their IP address, anything that you say to the police will be pretty much useless.
With this software, you will be able to make deep inspections of your platforms and you will be receiving detailed analysis about everything that’s currently happening to your network. A great choice for smaller businesses and SME’s.
5. Webroot
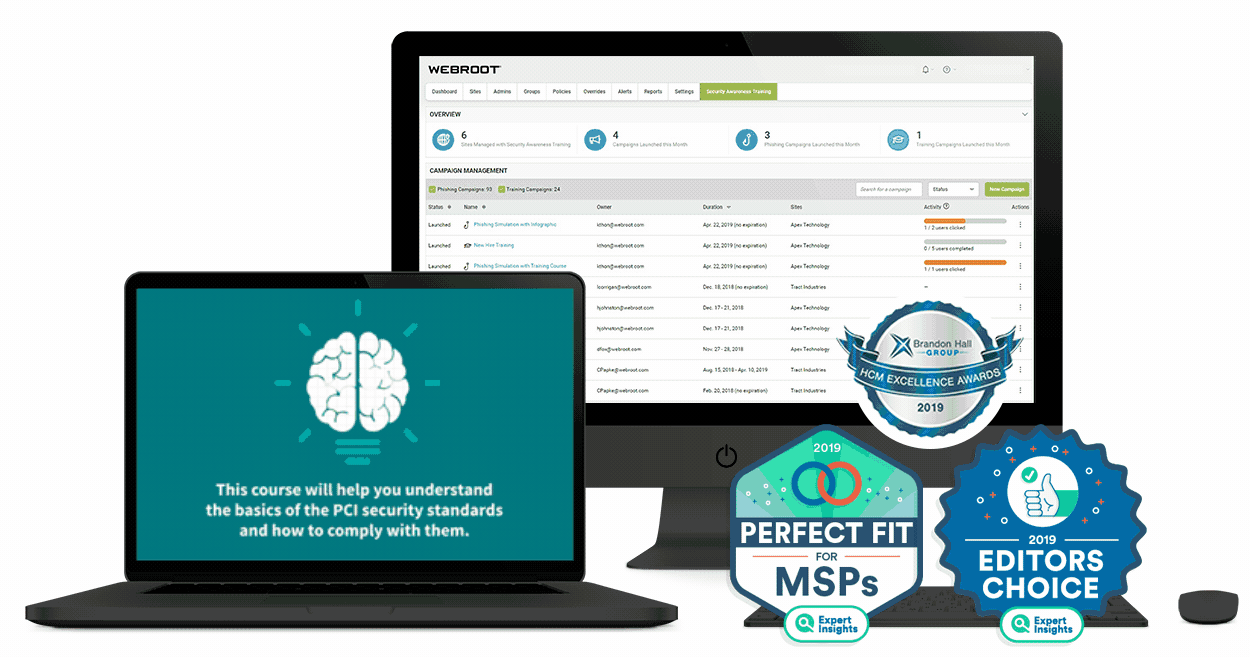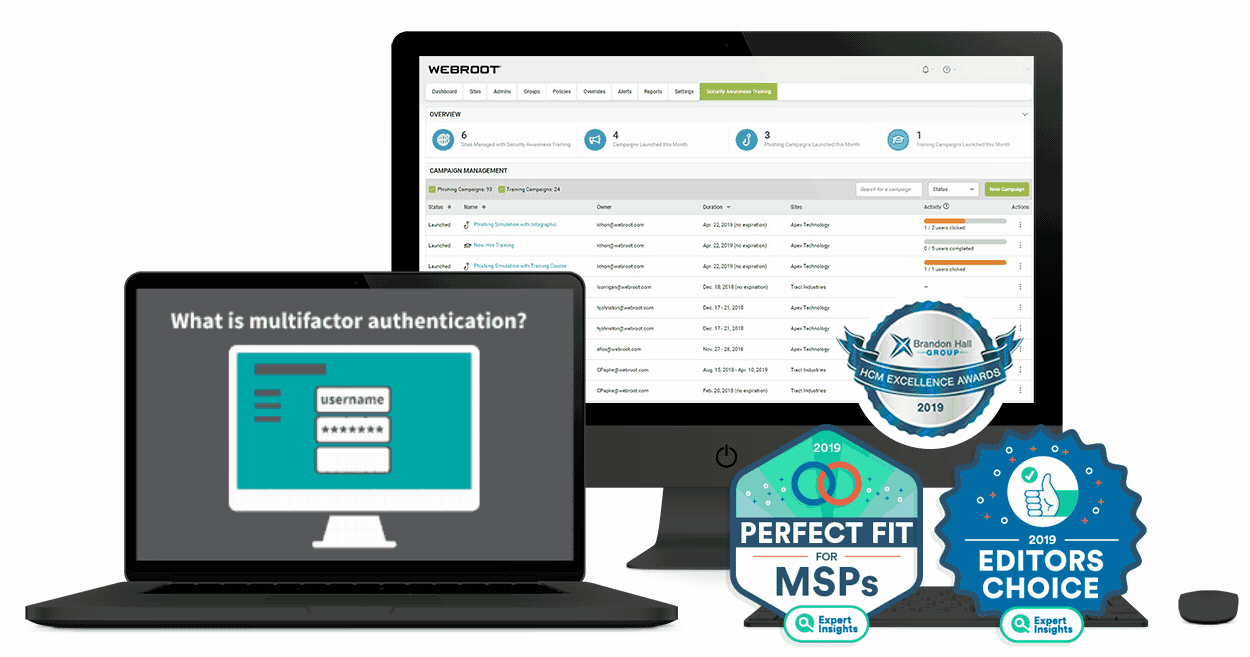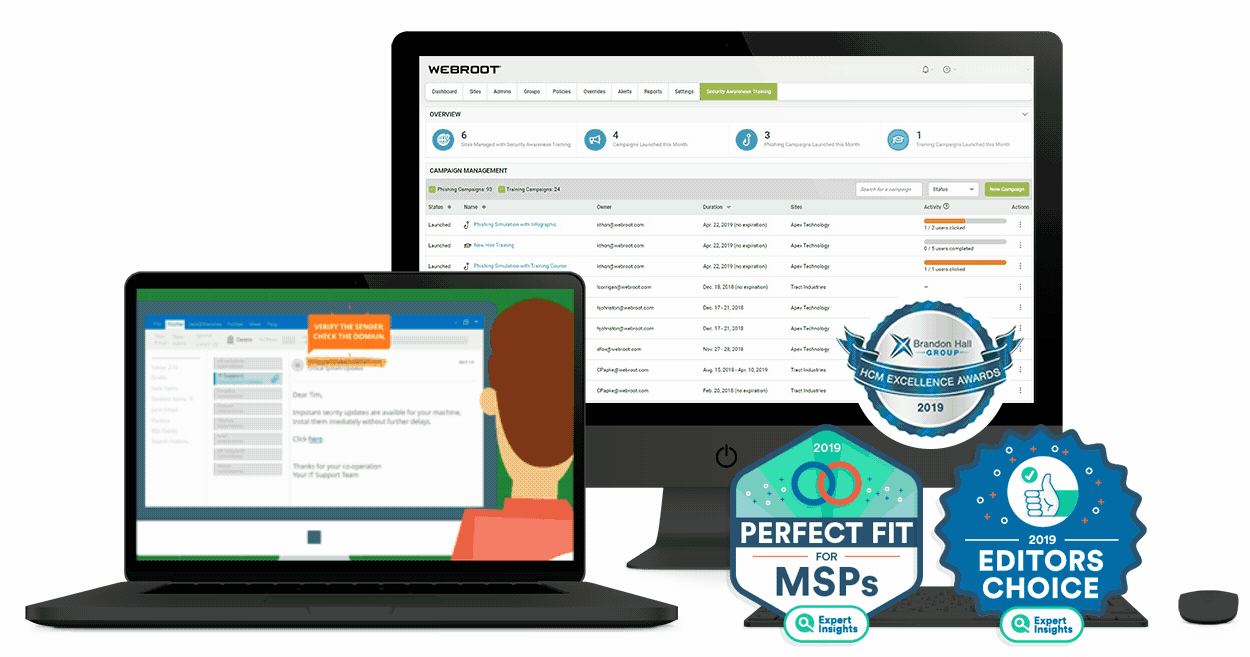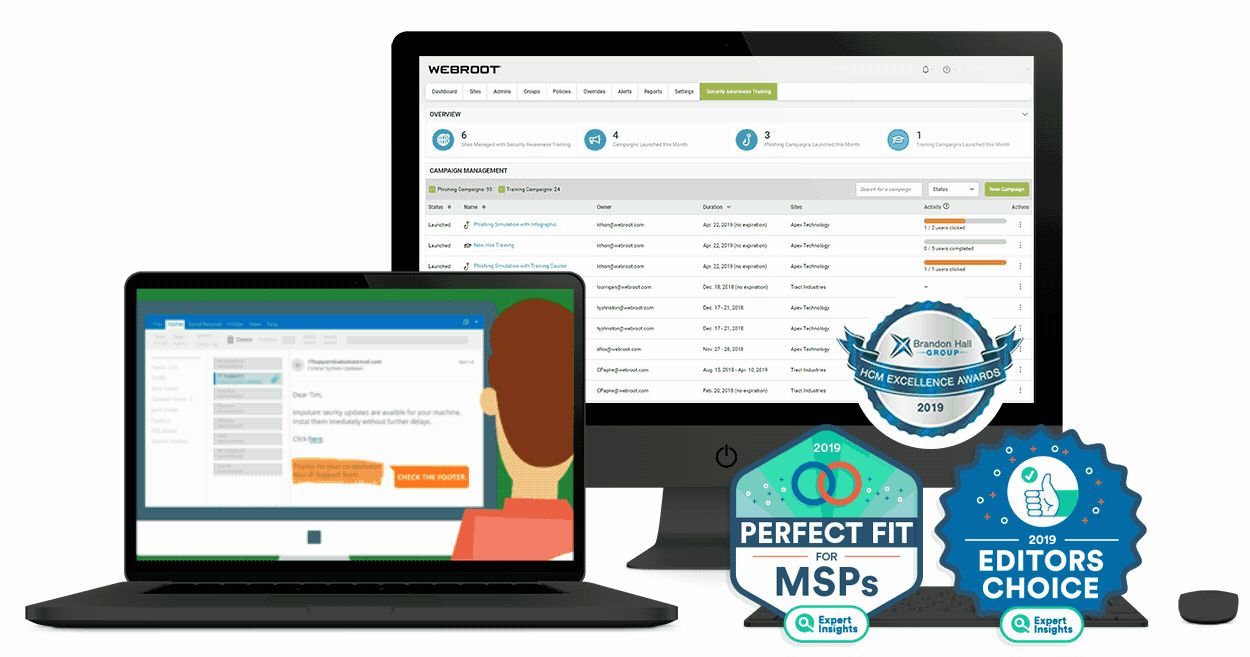
Webroot has been around for quite some time, and it is one of those computer programs that don’t cost a lot but they help you save so much by preventing any possible cyber-thefts or data exposure. When a certain business gets their data stolen, it can cost millions of dollars, so what are thirty bucks a year compared to a price like that? Webroot allows you to connect multiple devices on it, but you will have to get a separate license for all of them, which is not expensive at all.
It’s a cloud-based platform and you will be able to have real-time protection against any type of a threat lurking on your network if you decide to set it up in your business. It can work with almost any device that you can think of, so definitely give it a try if you are currently looking to improve your safety online.